Romain Thomas
Security Engineer
Reverse Engineering
Tooling
Code Obfuscation
Training
I'm a security engineer interested in reverse-engineering, code obfuscation, software protections, and tools development.
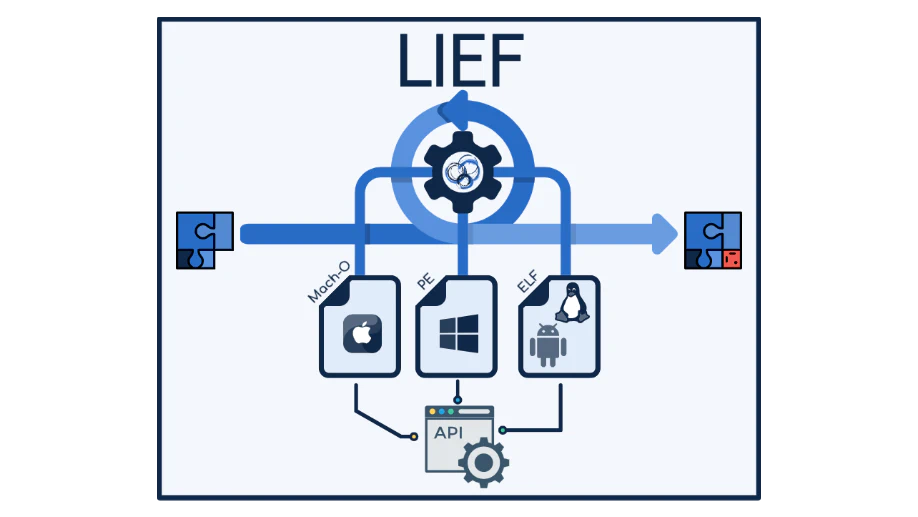
I develop and maintain LIEF, a library to parse and manipulate executable formats and I'm also working on Open-Obfuscator, a free and open-source obfuscator for mobile applications.
I enjoy going back and forth between reverse-engineering and tooling. I started at Quarkslab back in 2016 where I had the chance to work on various topics from JTAG ports detection to the support of AArch64 in QBDI. I also participated in the bootstrapping of an Android training covering both: system internals and app analysis. I left the company in 2021 to work on the security of banking applications. This new topic involves code obfuscation and software protection analysis from the perspective of EMVCo certifications.
Interests
- Reverse engineering
- Cryptography
- Executable file formats
- Mobile applications & internals
- Obfuscation
- Privacy
- Protocols Analysis
Blog Posts

iCDump: A Modern Objective-C Class Dump
This blog post introduces iCDump, an new Objective-C class dump based on LLVM
Open-Obfuscator: A free and open-source obfuscator for mobile applications
This blog post introduces open-obfuscator, a new open-source project to obfuscate mobile applications.
Part 2 – iOS Native Code Obfuscation and Syscall Hooking
This second blog post deals with native code obfuscation and RASP syscall interception
Projects

Android Runtime Restrictions Bypass (PoC)
Android application that disables Android restrictions without root privileges
Publications
Conferences & White Papers
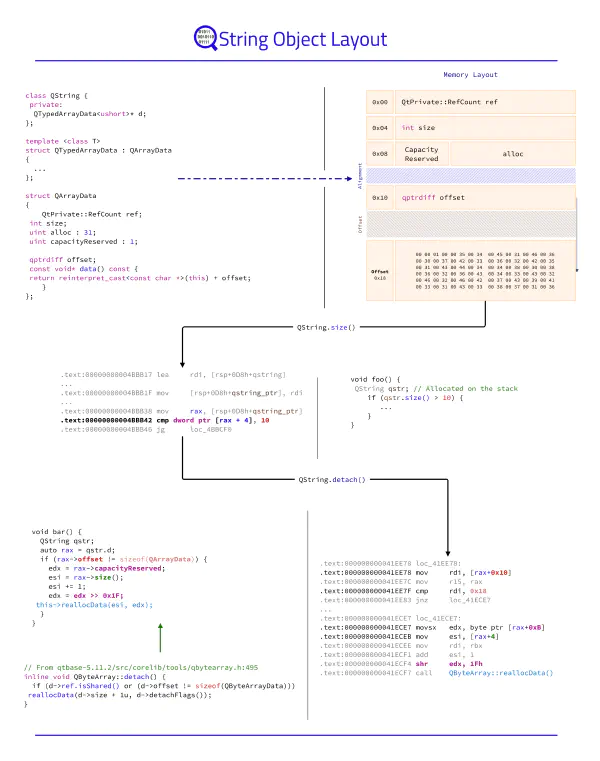
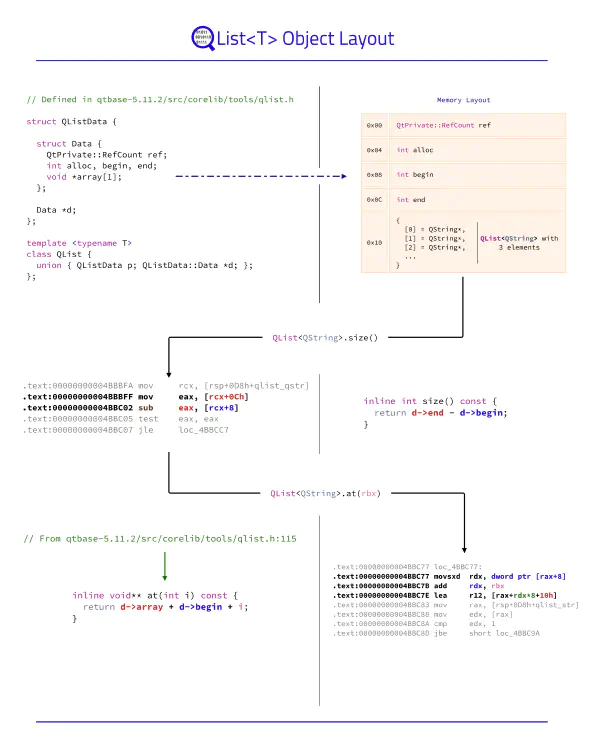
The Poor Man's Obfuscator
The purpose of this publication is to present ELF and Mach-O transformations which impact or hinder disassemblers like IDA, BinaryNinja, Ghidra, and Radare2.
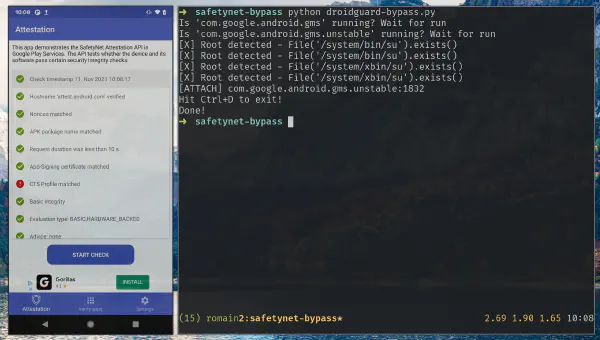
DroidGuard: A Deep Dive into SafetyNet
SafetyNet is the Android component developed by Google to verify the devices’ integrity. These checks are used by the developers to prevent running applications on devices that would not meet security requirements but it is also used by Google …
PGSharp: Analysis of a Cheat Engine on Android
PGSharp is a cheating app for PokemonGO that works on non-rooted devices. This talk introduces its functionalities and the protections used to prevent reverse-engineering.
Trainings & Workshops
Work Experience

QuarksLab
Security EngineerI worked on the following topics:
- Code obfuscation
- Reverse engineering
- Android
- Software protections
- Tools development (LIEF, QBDI, QBDL, …)
Android Trainer
I bootraped and I gave an Android training which aims at providing keys to analyze Android applications as well as their interactions with the system.
This training was covering the following topics:
- Malware analysis
- Android Runtime and file formats (DEX, ART, OAT, ODEX, VDEX, ELF)
- IPC and Binder
- Boot process
- Securities (dm-verity, SELinux, …)
- Protections (Obfuscation, packer, anti-debug, …)
- …
The complete syllabus is available here: https://quarkslab.com/training-android-applications/
Badge - Introduction to executable formats
This one day course is an introduction to executable formats in order to be more efficient when reverse engineering.
The course is focused on the PE and ELF formats.
QuarksLab
InternThis internship was about the development of LIEF: A library to parse and modify executable file formats. The project has been open-sourced few years later.
During this intern, I also developed an Android packer to protect native libraries.


QuarksLab
InternThis internship was about JTAG, and more precisely, how to discover JTAG ports on embedded systems (routers, 4G Internet key, …)
- Development of a JTAG testing tool
- Use of Bus Blaster and JTAGulator with the openOCD library.