Romain Thomas
Security Engineer
Reverse Engineering
Tooling
Code Obfuscation
Training
I am a security engineer with a strong interest in reverse-engineering, software protection and obfuscation.
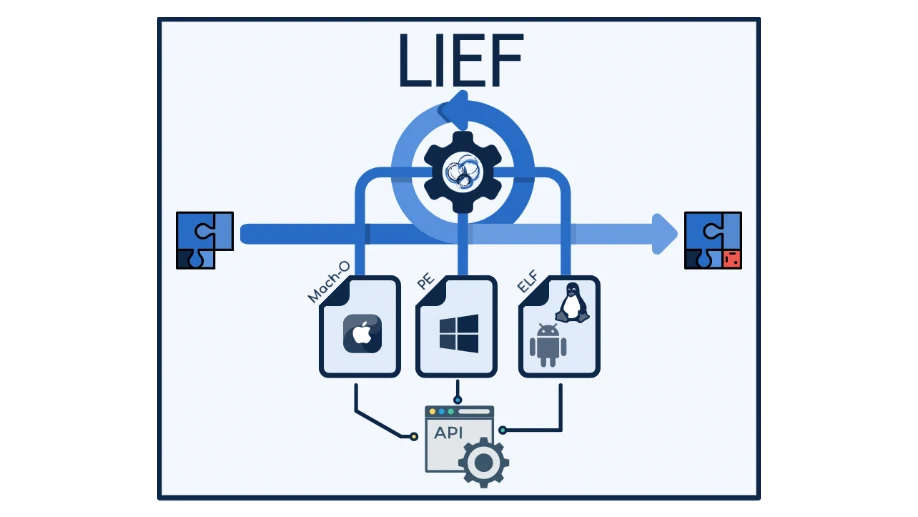
I am the author and maintainer of LIEF, a library used to parse and manipulate executable formats. In 2022, I initiated Open-Obfuscator a free and open-source obfuscator for mobile applications.
I enjoy navigating between development and reverse engineering.
With that in mind, I have contributed to various open-source projects like
QBDI, QBDL or open-obfuscator and reverse engineered
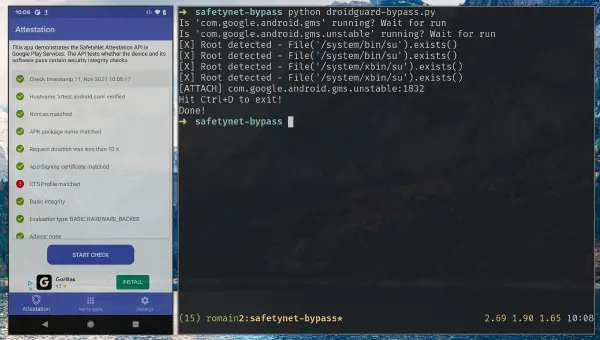
Safetynet,
iXGuard,
Arxan,
DexProtector,
and
cheats.
My journey started at Quarkslab in 2016 with a focus on Android, but since then,
I have had the chance to dig into other platforms (iOS/macOS, Windows)
through the lens of reverse engineering or obfuscation.
Interests
- Reverse engineering
- Cryptography
- Executable file formats
- Mobile applications & internals
- Obfuscation
- Privacy
- Protocols Analysis
Blog Posts
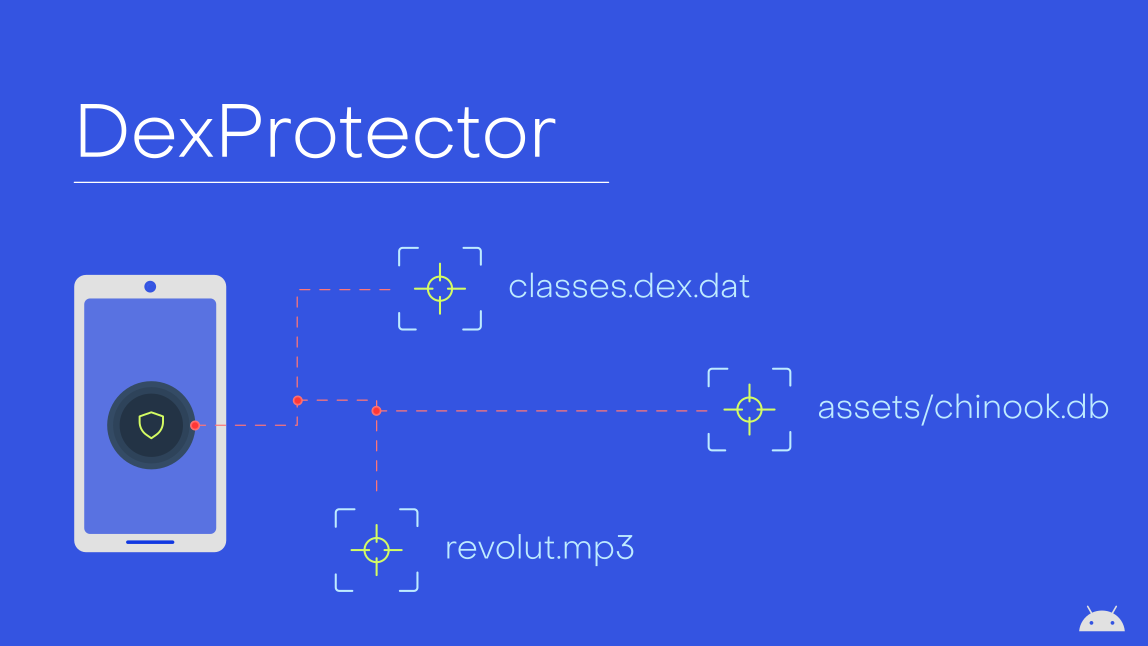
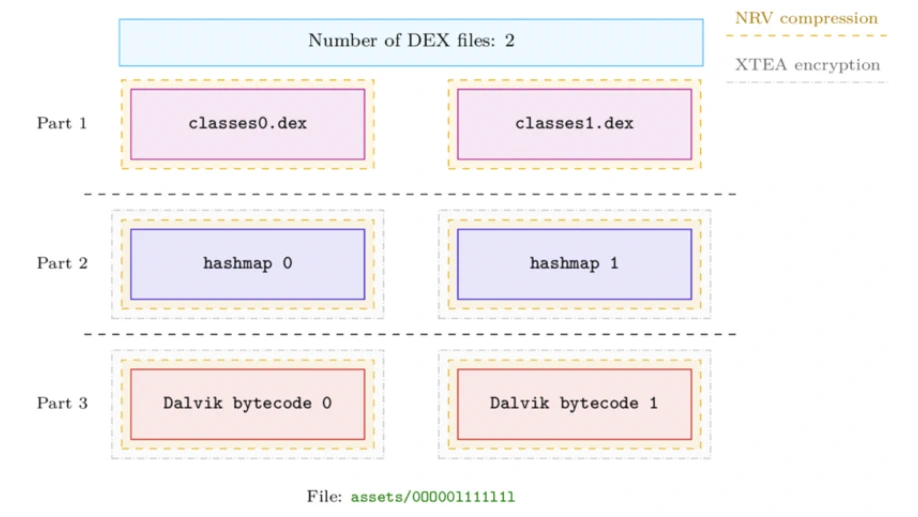
A Glimpse Into DexProtector
This blog post provides a high-level overview of DexProtector’s security features and their limitations

Fuzzing Windows ARM64 closed-source binary
This blog post introduces coverage-guided fuzzing with QBDI and libFuzzer targeting Windows ARM64.

Instrumenting an Apple Vision Pro Library with QBDI
This blog post demonstrates how to extract liblockdown.dylib from the visionOS dyld shared cache to be instrumented with QBDI on an Apple M1.
Projects

Android Runtime Restrictions Bypass (PoC)
Android application that disables Android restrictions without root privileges
Publications
Conferences & White Papers
The Poor Man's Obfuscator
The purpose of this publication is to present ELF and Mach-O transformations which impact or hinder disassemblers like IDA, BinaryNinja, Ghidra, and Radare2.
DroidGuard: A Deep Dive into SafetyNet
SafetyNet is the Android component developed by Google to verify the devices’ integrity. These checks are used by the developers to prevent running applications on devices that would not meet security requirements but it is also used by Google …
PGSharp: Analysis of a Cheat Engine on Android
PGSharp is a cheating app for PokemonGO that works on non-rooted devices. This talk introduces its functionalities and the protections used to prevent reverse-engineering.