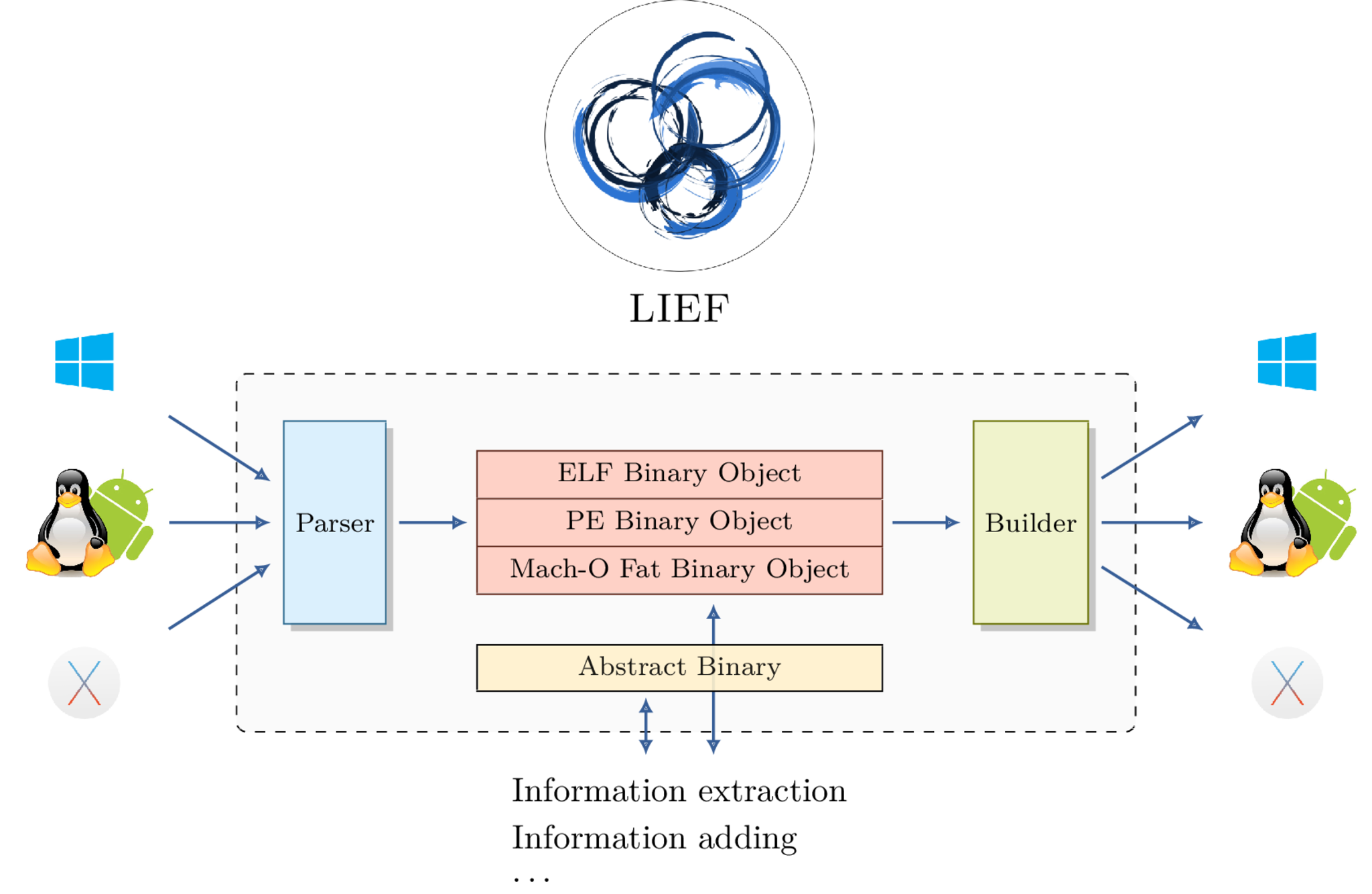
When analyzing executable, the first layer of information is the format in which the executable is wrapped. It turns out that a lot of tools and libraries exist to analyze and instrument machine code wrapped by the format, but there is not such library to handle the three mainstream executable formats and to both read and modify these formats. LIEF has been developed to that end.
In the talk we will explain the rationale behind LIEF architecture choices, what LIEF allows to do and have a look at use cases.
LIEF is a cross platform library and it can be used through a Python, C++ and C API. The library enables to parse standard structures as well as more complex ones like PE Signature (Authenticode) and ELF hash table. As use cases we can inject code into a binary or a library, we can also redirect the control flow to hook functions and it can be used to obfuscate some parts of a binary. Another feature of LIEF is that common characteristics of these formats are factorized so that we can develop a single script which works for the three formats.
Slides of the talk given at RMLL
You can also grab the slides of the talk given at Cybersecurity France-Japan: 17-04-cybersecurity-frjp-LIEF.pdf